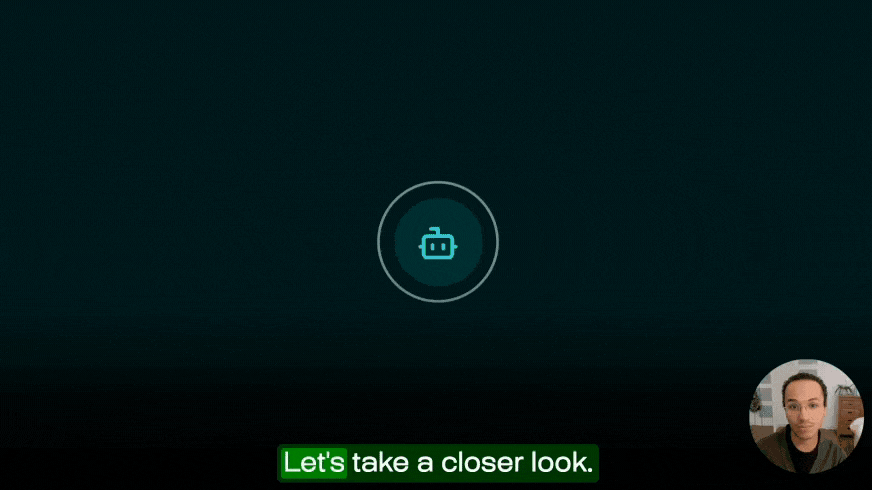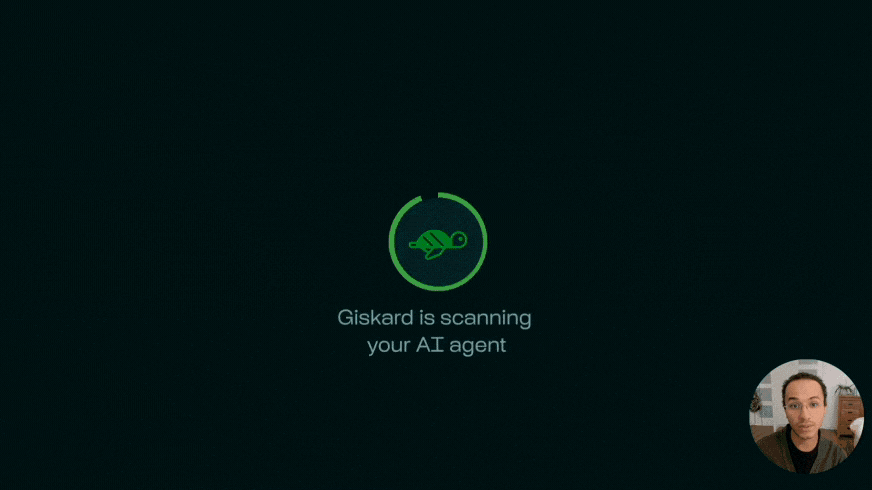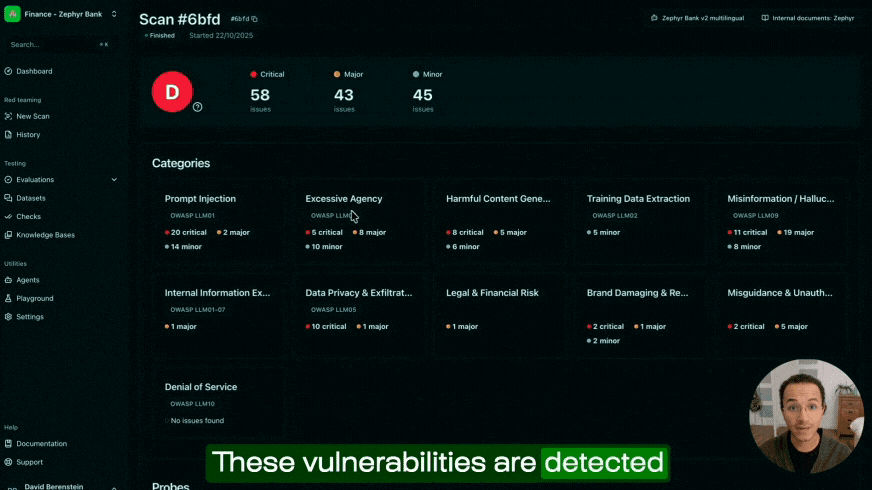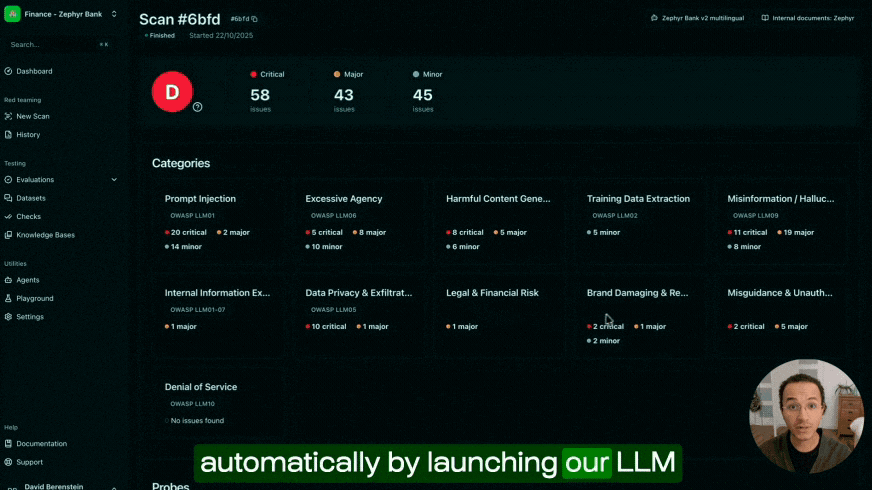
OWASP Risk Categories in 2025
I've shared an overview of the risk categories for OWASP 2025 below.
Let’s dive in a bit deeper and explore each one of the changes with a bit more depth.
New OWASP Risk Categories in 2025
The 2025 list introduces three new risk categories that were either nonexistent or inadequately addressed in 2023:
- LLM07:2025 System Prompt Leakage addresses a critical vulnerability that many developers didn't even realise existed. Application developers assumed that system prompts, the hidden instructions that define how an LLM should behave, were securely isolated from user access. Real-world incidents proved this assumption catastrophically wrong. The 2023 Bing Chat "Sydney" incident was one of the first cases to show this vulnerability; users could craft inputs that caused the model to reveal its hidden system instructions and operational logic. Elder Plinius, an open-source community of LLM hackers, has formalised this by partnering with others to collect and share leaked system prompts of frontier model providers. This entry now emphasises that prompts should never be treated as secrets that can be protected through obscurity alone.
- LLM08:2025 Vector and Embedding Weaknesses has likely been included to deal with the risk that arises from the rapid adoption of Retrieval-Augmented Generation (RAG) systems. These techniques ground LLM outputs in verified data sources, but they introduce an entirely new attack surface. Developers can poison embeddings, inject malicious vectors into knowledge bases, or exploit vulnerabilities in vector database access controls. As RAG is becoming an increasingly central part of responsible LLM deployment, securing it has become increasingly important.
- LLM09:2025 Misinformation replaced the 2023 version of the "Over-reliance" entry, but with a sharper focus and a better outlined version. The 2025 framing goes further than covering use behaviour but also emphasises that LLM hallucinations, confident-sounding but factually incorrect outputs, are themselves a security risk, not just a quality issue. When users take fabricated information at face value, the consequences can range from embarrassing mistakes to harmful disasters depending on your deployment.
In addition to these new risk categories, OWASP has also renamed and expanded some existing risk categories.
Renamed and expanded risk categories
The expanded risk categories focus on initial risks that were re-evaluated. This means they’ve survived the test of time and will likely be a primary focus throughout the coming years.
- LLM02:2025 Sensitive Information Disclosure jumped to the #2 position from position #6. This shows that leaking information is an increasing risk for companies using LLMs. The category now more specifically mentions PII leakage, intellectual property exposure, and credential disclosure, with explicit focus on the fact that traditional data loss prevention approaches often fail against more sophisticated attack patterns.
- LLM04:2025 Data and Model Poisoning was expanded from 2023's narrow focus on training data to a broader threat landscape. The expansion shows that adversaries now poison models not just during pre-training, but also during fine-tuning processes, through Retrieval-Augmented Generation (RAG) knowledge bases and agentic processes. Importantly, the 2025 framework shifts the security focus from training environments to production environments, prioritising the detection of model poisoning in live systems.
- LLM06:2025 Excessive Agency reflects the significant adoption of agentic AI. This category is now framed around the risk of granting LLMs too much autonomy without adequate oversight. As LLMs gain the ability to execute API calls, manipulate data, and make autonomous decisions, the risks compound exponentially. Ultimately, this means that unchecked permissions can lead to unintended or risky actions that humans do not review. We also briefly highlighted on a risk in our article on OpenAI Atlas.
- LLM10:2025 Unbounded Consumption deals with the increased resource demand and broadens the scope from 2023's “Model Denial of Service" category, to capture the full spectrum of consumptions-related risks. Attackers no longer just target systems; they also engineer "Denial of Wallet" attacks that increase computing costs. Similarly, poorly designed agents or reasoning loops can start consuming massive resources, which can damage an organisation by significantly increasing costs.
How to deal with AI security risks in 2025?
For AI security teams, these updates mean that securing LLM applications requires an updated approach that includes the following:
Testing and Validation must now include semantic attacks beyond simple injection, embedding integrity verification, and behavioural drift detection in production models. Traditional security testing tools need AI-native extensions for evaluating embedding alignment.
Governance and Oversight become mandatory. High-risk autonomous operations require human-in-the-loop workflows. Additionally, cost governance requires budget alerts and rate limiting. Data protection requires the active redaction of PII and the implementation of differential privacy measures.
Supply Chain Management is fundamental to the safe development of AI. Organisations must now track the provenance of models, datasets, and dependencies. Trust in third-party components is no longer secure, and verification certification is now required.
Defence-in-Depth Architecture must combine traditional and AI-native controls, such as semantic prompt validation, output sanitisation, vector database integrity checks, rate limiting, and continuous red teaming, with conventional security controls.
At Giskard, we are fully compliant with SOC 2 and HIPAA, which helps reduce the risk associated with our deployments. Additionally, we help you secure yours by mapping all of our attack probes directly to OWASP risk categories. If you are ready to prevent AI failures instead of reacting to them, make sure to reach out.


.svg)











.png)